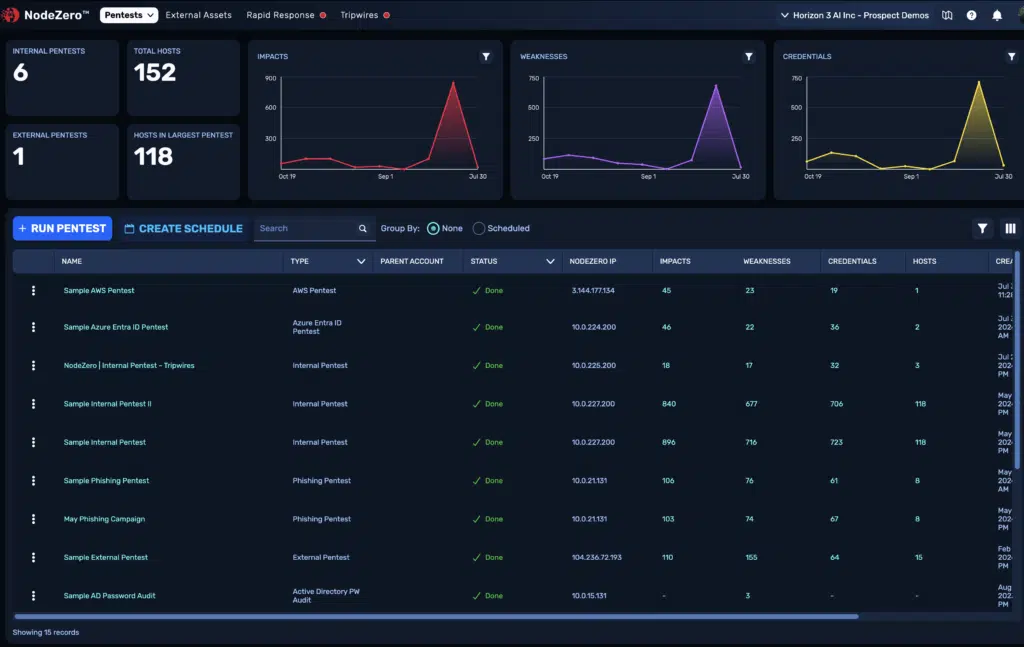
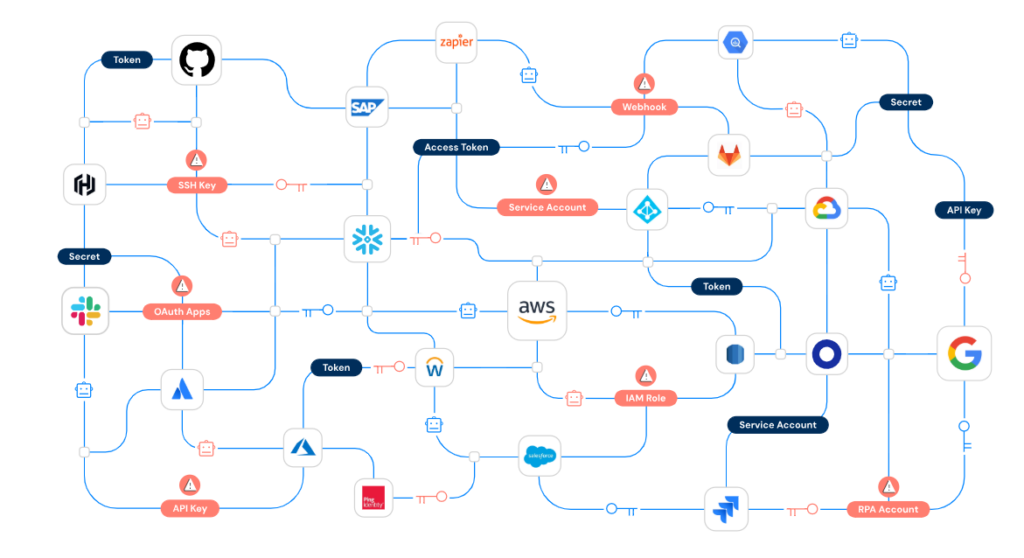
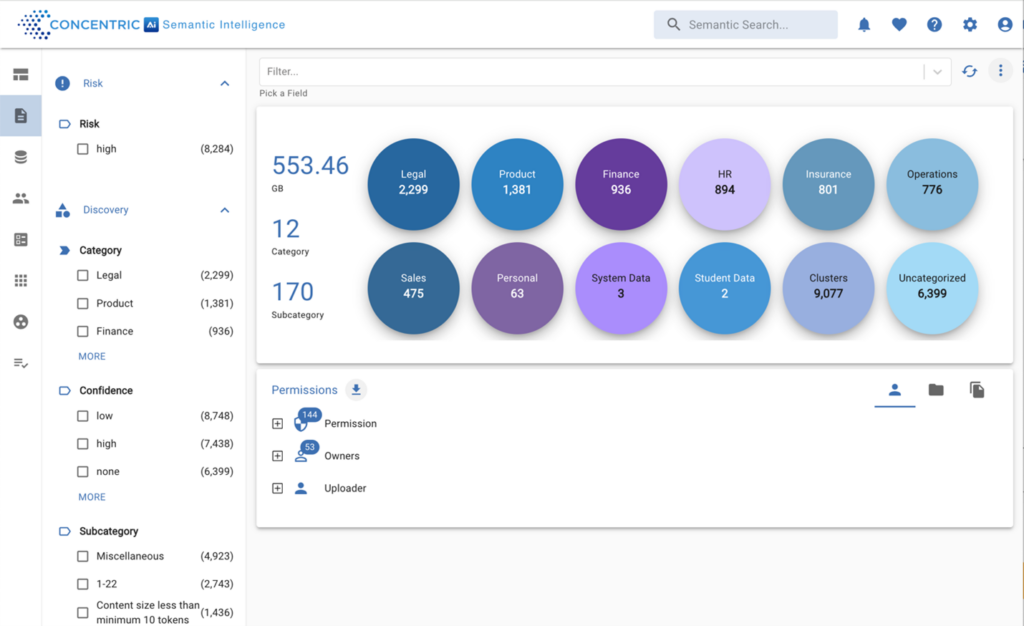
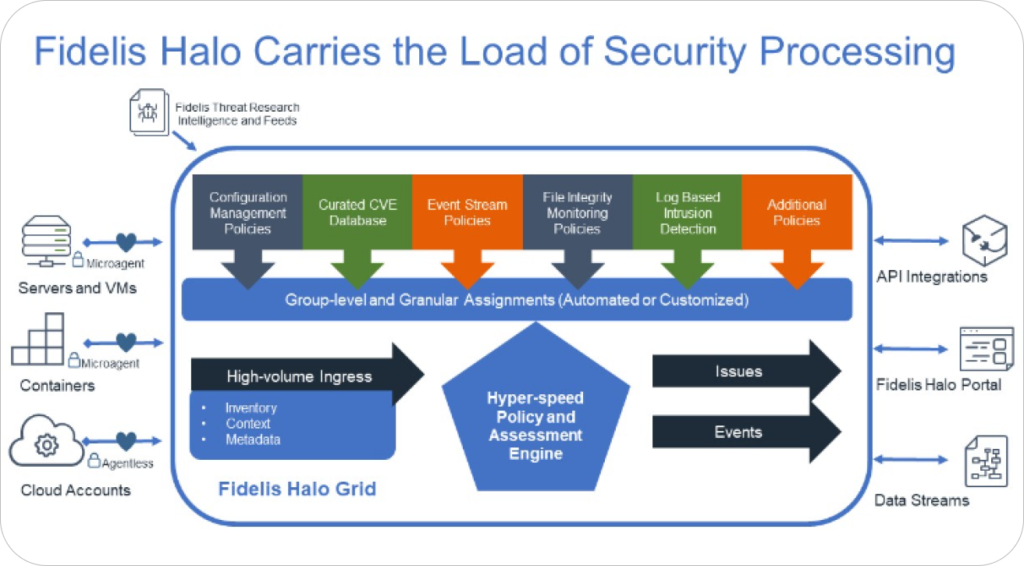
ITR Cyber is a Cyber Security Reseller that helps UK businesses outsmart ransomware, phishing and other AI driven threats with consulting, XDR and vendor backed solutions all under one roof. Their specialists bring 130 + years of collective cyber and hardware experience to every project, giving you a single, trusted partner for risk assessment, prevention and rapid response.
What ITR Cyber Offers
Cyber Security Consulting
Gap analysis and risk scoring
Tailored road-maps aligned to NCSC best practice
Incident-response planning and tabletop exercises
Managed & Co Managed Solutions
XDR / EDR: Extended coverage that neutralises fileless attacks before encryption.
CNAPP: Cloud-native application protection for AWS, Azure and GCP.
Advanced Threat Protection: AI-driven anomaly detection with 24 × 7 SOC eyes-on-glass.
Vendor Ecosystem
ITR Cyber is a Cyber Security Reseller for 15 + leading vendors—including Morphisec, Horizon3.ai and BlackFog—so you get enterprise-grade tools on one bill.
Why It Matters
-
Gartner projects information-security spend will rise to $212 bn in 2025—up 15 % YoY. securityreviewmag.com
-
By 2027, 17 % of cyber-attacks will leverage GenAI, raising the bar for detection. crn.com
FAQ's
They audit and their vendors can deploy zero-trust controls and can monitor 24 × 7 to block attacks.
Ransomware is a type of malicious software, or malware, designed to encrypt a victim’s data or lock them out of critical systems. Once the files are encrypted, attackers demand a ransom payment, often in cryptocurrency, to restore access. Ransomware has become one of the most financially devastating and fast-spreading cyber threats, affecting individuals, businesses, and governments alike.
A ransomware attack occurs when a cybercriminal successfully infects a system or network with ransomware. During the attack, the ransomware encrypts data or locks down the victim’s device, effectively holding their information hostage. Attackers then present a ransom demand, often with a strict deadline, and threaten to permanently delete or expose sensitive information if payment is not made.
Ransomware typically works in several stages:
- Infiltration: Attackers gain access through phishing emails, malicious attachments, software vulnerabilities, or other deceptive tactics.
- Encryption: Once inside the system, ransomware encrypts critical files, rendering them inaccessible.
- Demand and Coercion: The victim is shown a ransom demand to regain access to the data, often with a time-sensitive ultimatum.
- Potential Further Damage: Even after payment, some attackers may install additional malware, sell data, or leave the system vulnerable.
By using innovative approaches like Morphisec’s MTD, organisations can disrupt this process early, preventing ransomware from successfully executing its encryption step.
Ransomware locks or encrypts the victim’s files or system, denying access until a ransom is paid. Some ransomware variants, like “double extortion” ransomware, not only encrypt but also steal data, threatening to expose sensitive information if the ransom isn’t paid. Ransomware can halt entire business operations, leading to loss of revenue, reputation damage, and potentially significant recovery costs.
Ransomware can spread in multiple ways, including:
- Phishing Emails: Cybercriminals use phishing emails with malicious attachments or links to infect a user’s device.
- Drive-By Downloads: Simply visiting a compromised website can cause ransomware to download and infect the system.
- Exploiting Software Vulnerabilities: Unpatched or outdated software can provide an entry point for ransomware.
- Lateral Movement in Networks: Once inside a network, ransomware can move from one system to another, potentially affecting the entire organisation.
By adopting advanced technologies like Morphisec’s Moving Target Defense, organisations can prevent ransomware from executing, stop it from spreading, and safeguard their networks from these high-impact attacks.
To prevent ransomware effectively, it’s essential to use a proactive and adaptable solution, and this is where Morphisec stands out. Morphisec uses Moving Target Defense (MTD) technology, a unique approach that continuously shifts and scrambles the attack surface. Here’s why Morphisec offers advantages over traditional solutions:
Proactive Threat Prevention: Unlike conventional antivirus or EDR solutions that rely on signatures or patterns, Morphisec’s MTD technology makes endpoints unpredictable to attackers, preventing ransomware from executing even if it’s undetected by traditional tools.
Protection Against Fileless Attacks: Ransomware increasingly uses fileless attack methods, running in-memory and avoiding files that are easy to detect. Morphisec’s MTD is designed to counter in-memory threats, making it particularly effective against these advanced, stealthy ransomware tactics.
Lightweight and Seamless Operation: Morphisec operates without the need for constant updates, heavy scanning, or signature-based detection, meaning it protects without impacting system performance or slowing down users.
Choosing Morphisec over other vendors offers a distinctive advantage: it provides zero-day protection by dynamically preventing any predictable foothold, reducing the likelihood of ransomware attacks at a level that traditional signature-based defenses cannot match.
Latest Insights in Cyber Security
Cyber attack at Christmas on the rise
The Rise of Cybercrime During the Festive Season and How Leading Cybersecurity Vendors Can Help
Emerging Cyber Threats in 2024: What’s New?
1. AI-Generated Attacks at Scale Artificial Intelligence (AI) has proven to be a double-edged sword in
The Importance of Cyber Security Consulting
Discover why investing in cyber security consulting is vital for your business.